From Ciphers to Computers: Enigma and the Cryptography Revolution.
Alessandra Bertini - 2024-06-12
Starting with the ancient Vigenère cipher, this article delves into the historical and contemporary importance of cryptography, examining Enigma, the World War II encryption tool, and its evolution to modern data security technologies.
Within this article we will delve into the world of cryptography, turning our gaze especially to Enigma, an encryption tool used primarily during World War II. We will learn about its structure, its use and how cryptography of the past influenced it.
Index
- Introduction to Cryptography: From Ancient Ciphers to Enigma
- Enigma: Toward Modern Cryptography
- Contemporary evolution and future challenges of cryptography
- Conclusions and future prospects
In an era where technology permeates every aspect of our lives, data protection becomes essential to prevent unauthorized access. Encryption, once the domain of devices such as Enigma during World War II, is now vital for applications that handle sensitive information.
This article explores how cryptography, seemingly invisible but ubiquitous in our digital interactions, has evolved from historical tools such as Enigma to sophisticated systems that define security in the digital age. We take a look back to the past to better understand our present and foreshadow the future of cybersecurity.
Introduction to Cryptography: From Ancient Ciphers to Enigma
Introduction to Cryptography
Before we start talking about Enigma, let's start with the basics. Let's define as a first step what cryptography is:
Cryptography, from the Greek for "secret writing," is a technique of representing a message so that the information it contains can be known, and therefore read, only by the recipient. Its history, starting from ancient ciphers such as the Atbash to modern use in computers and the Internet, shows how technology has continued to influence data security.
In 1918, Arthur Scherbius patented Enigma, a machine using polyalphabetic methods derived from Vigenère's table and Leon Battista Alberti's cipher. Enigma marked a significant evolution in cryptography, combining ancient principles with mechanical innovations, and laying the foundation for modern encryption techniques.
Enigma, therefore, not only ended the dominance of pen and paper in cryptography, replacing them with the use of mechanical rotors for advanced encryption, but also set a precedent for modern information security systems, demonstrating the crucial importance of cryptography in today's increasingly connected and technological world.
A rotor of the Enigma machine
Source: Wikipedia
A journey to the roots of cryptography
The journey through the history of cryptography leads us to recognize the importance of two fundamental tools: the table of Vigenère and the cipher of Leon Battista Alberti. These methods laid the foundation for the development of more complex cryptographic systems, such as Enigma.
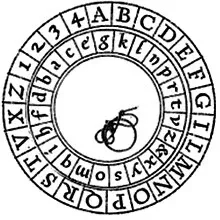
- Vigenère's table., introduced by Blaise de Vigenère, used different sequences of letters, or alphabets, that alternated based on a keyword. This polyalphabetic system complicated decryption attempts because the same letter could be encrypted in different ways depending on the position and corresponding letter of the key. The key, repeated over the original text, determined which alphabet to use for each letter in the message, making this cipher more secure than previous monoalphabetic systems.
The table of Vigenère
Source: Cryptology
- Leon Battista Alberti's cipher., on the other hand, represents a milestone in cryptography for its innovative use of cipher disks, which prefigure the Enigma rotors. Alberti designed his disks with two concentric alphabets: a fixed outer one and an inner one that could rotate. This allowed users to systematically change the alphabet used during encryption, a technique that significantly increased message security.
Cipher disc
Source: Wikipedia
Both of these methods directly influenced the design of Enigma. Enigma's rotors, analogous to Alberti's discs, changed their position with each letter typed, creating an ever-changing cipher pattern similar to the effect produced by Vigenère's table. The complexity and security of Enigma were greatly enhanced by the combination of multiple rotors, each acting as an independent alphabet within an extremely advanced polyalphabetic system.
The link between these ancient ciphers and Enigma demonstrates not only the evolution of cryptography from relatively simple tools to elaborate machines, but also how the basic principle of cryptography-protecting information by making it inaccessible to the unauthorized-has remained unchanged over the centuries.
Enigma: Evolution of a Cryptographic Revolution
In the digital age, cryptography is not just an ancient practice revisited; it has become an essential component of our daily lives. This chapter explores the evolution of cryptography from the Enigma machine used during World War II to the complex security architectures that protect our most sensitive data today.
Birth and development of Enigma
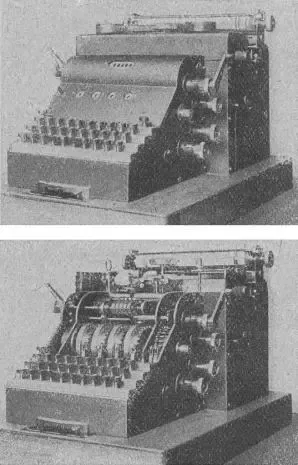
In 1918, German engineer Arthur Scherbius patented Enigma, a cryptographic machine that marked a revolution in the field of data security. Initially conceived as a series of prototypes called Enigma-Probemaschinen, these machines were the forerunners of modern cryptographic systems. Early commercial versions, such as the Die Handelsmaschine, introduced in 1923, were bulky typewriter-like machines, complete with internal rotors and a configuration that allowed both encryption and decryption of messages through an adjustable handle.
Reproduction of the Enigma trademark
Source: Wikimedia
Early versions of Enigma and their evolution
Early versions of Enigma were rudimentary machines that used light bulbs to display ciphered characters, a novelty at the time. However, structural problems and the need for greater security led to the development of improved versions such as the Enigma A, introduced in 1924. This model incorporated a reflector, a component that allowed encryption and decryption using the same mechanism, thus making it easier to use and improving operational efficiency.
Enigma during the Second World War
With the advent of World War II, the Enigma I became the standard for the German military. This advanced model included up to five interchangeable rotors, each with different wiring for complex encryption schemes. The ability to change the configuration of the rotors daily greatly increased the security of communications.
Source: Cryptomuseum
Evolution of the Enigma
However, the complexity of Enigma did not guarantee inviolability; the work of cryptanalysts such as Marian Rejewski, along with the contributions of Alan Turing and the Bletchley Park team, led to the development of advanced decryption techniques, culminating in the creation of the "Bomb" machine, capable of deciphering Enigma codes. For those interested in exploring this fascinating story further, the film "The Imitation Game" offers an engaging and accessible depiction of Turing and his team's achievements during the war.
Contemporary evolution and future challenges of cryptography
Over the years, cryptography has evolved significantly, driven by technological innovation and the growing need to protect data in increasingly digitized and connected environments. From mechanical machines such as Enigma to today's complex algorithms that exploit advanced mathematical principles, cryptography remains critical to ensuring information security.
Modern cryptography uses algorithms that can be divided into two main categories: symmetric and asymmetric. Symmetric algorithms, such as AES (Advanced Encryption Standard), use the same key to encrypt and decrypt messages, offering speed and efficiency for protecting large volumes of data. On the other hand, asymmetric encryption, such as Rivest-Shamir-Adleman (RSA)-based encryption, employs a separate key pair for encryption and decryption, which is essential for secure Internet communications, such as online financial transactions.
Impact of quantum computer on cryptography
One of the most significant challenges for contemporary cryptography emerges with the development of quantum computers, which promise to revolutionize many aspects of computing through their ability to perform calculations at previously unimaginable speeds. Quantum computers have the potential to disrupt many of the cryptographic algorithms currently in use, including those that rely on the difficulty of factoring large numbers, a principle underlying RSA.
To address this emerging threat, researchers are developing post-quantum cryptography, which includes new algorithms designed to be secure against attacks carried out by quantum computers. These new approaches exploit even more complex mathematical problems that even quantum computers find difficult to solve, thus ensuring continued data protection even in this new era.
Conclusions and future prospects
The history of cryptography, from Enigma to the present day, is a testament to humanity's continuing effort to protect its information. As we approach the era of quantum computing, cryptography will remain a field of intense research, innovation and, inevitably, a race between encryption and decryption techniques. The security of our personal data, communications and critical infrastructure will increasingly depend on our ability to adapt and innovate in the face of the challenges posed by new disruptive technologies.
Computational Cryptography
Source: Medium
In conclusion, just as Enigma marked an epoch in the history of data security, future developments in cryptography will be equally decisive in shaping the security landscape in the digital and quantum age, underscoring a relentless need for evolution and adaptation in response to emerging computational capabilities.
Alessandra Bertini
I have been working at Ulixe since 2023 as a Back-End software developer. My passion for computer science was born in school and continued in college. Upon completion of my studies I began my adventure as a programmer. When I am not developing I am in the mountains climbing peaks or comfortably sitting on the couch knitting.
See More Posts
Get in touch
Ulixe Group S.r.l. Copyright © Ulixe Group S.r.l. | Lungo Dora Pietro Colletta, 67, 10153, Turin, Italy | VAT IT03305250122 | Rea Number TO1173020